"Automate Vulnerability Discovery with Nuclei: A Comprehensive Guide to Enhance Cybersecurity"
Nuclei is a powerful and user-friendly vulnerability scanning tool created by projectdiscovery, designed to assist security professionals in automating the process of identifying security issues. Using straightforward YAML-based templates, Nuclei can automatically detect vulnerabilities across various protocols like HTTP, DNS, TCP, and more.
One of the standout features of Nuclei is its high level of customization, allowing security experts to tailor the scanning process to their specific needs. The heart of the tool lies in its extensive collection of vulnerability templates, which can be found on GitHub. These templates have been meticulously crafted by a community of over 100 security researchers and are actively maintained by projectdiscovery.
The templates cover a wide range of categories, making it easy to pinpoint vulnerabilities based on CVEs (Common Vulnerabilities and Exposures), exposed panels, potential takeovers, misconfigurations, technologies in use, default logins, and much more.
With its versatility, speed, and the continuous efforts of its dedicated community, Nuclei has become an invaluable asset in the arsenal of security professionals, enabling them to proactively identify and address potential security risks with ease.
Installation:
Before installing Nuclei, it is essential to ensure that Go programming language is installed on your system. To achieve a seamless installation process, you can use the following one-liner command:
"Ensure a smooth Nuclei installation by first verifying that you have Go language installed with this simple one-liner command."
In case you encounter any difficulties during the installation, you can always refer to the official website for further guidance and support.
Run the Command in linux terminal:
"sudo apt-get install golang"
Now, Ready to Install Nuclei? Execute the following one-liner command to get started:
"GO111MODULE=on go get -v github.com/projectdiscovery/nuclei/v2/cmd/nuclei"

Stay Up-to-Date with Nuclei: After installation, it's crucial to keep your tool current. Update Nuclei and its templates easily with the following command:
"nuclei -update-templates"

By staying updated, you ensure that Nuclei remains equipped to identify the latest vulnerabilities and security issues, bolstering your cybersecurity efforts.
Nuclei Usage Example:
1. Nuclei - Help Manual
nuclei --help

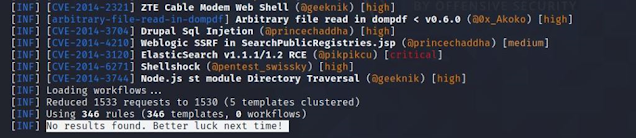
2. Run Nuclei against target to find target if vulnerable to CVEs present in Database
Note: If you have list of targets then include it in a file and run .
"nuclei -l targetlist_filename -t cves"

Note: Again you can Filter/Mark/Indicate the vulnerability based on its Severity levels[low,medium,high,critical]
"nuclei -l targetlist_filename -t cves -severity critical "
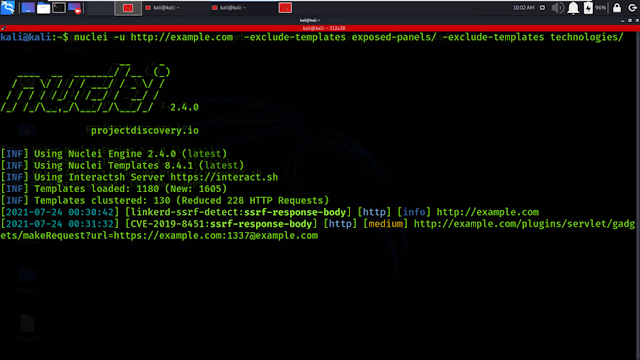
3. Run a Single Target
"nuclei -u targetwebsite.com"
4. Nuclei Templates:
List of Templates avaialable:-
- cves - tests target against all cves present in db.
- iot - finds vulnerability in iot devices.
- exposures - finds common information exposures/disclosures.
- technologies - finds vulnerable technology in target
- vulnerabilities - Checks for Vulnerabilities
- takeovers - Finds takeovers
- fuzzing - Performs Fuzzing
- helpers,
- dns - Performs testing on dns and finds related flaws
- file,
- miscellaneous,
- default-logins -Finds Default login pages/Credentials
- exposed-panels -Finds Exposed Panels
- workflows -To test Workflows
- misconfigurations - Finds Misconfigurations
In conclusion, Nuclei proves to be an indispensable and versatile vulnerability scanner, utilizing YAML-based templates to efficiently identify security issues across various domains such as Networks, Web Applications, and DNS-based misconfigurations. If you haven't experienced the benefits of this remarkable tool, I highly recommend adding it to your cybersecurity arsenal.
This basic tutorial provides a solid foundation to begin exploring Nuclei's capabilities. However, for a more comprehensive understanding and advanced usage, I encourage you to explore the official documentation of Nuclei, which offers an in-depth guide to fully harness the potential of this powerful tool.
Embrace Nuclei's capabilities to enhance your security practices, and by staying updated with the latest templates, you can effectively safeguard your systems and web applications from potential threats. Empower your security endeavors with Nuclei, and embark on a proactive journey towards fortifying your digital assets and ensuring a safer cyber environment.